Motivation
Bitcoin, Ethereum, Blockchain, DeFi, etc. are terms that are being thrown around a lot these days. You hear about it a lot on social media and on other places on the internet (especially when their prices are rising), but the vast majority of people do not know much about what they are or what they do.
My name is Harsh Strongman and I was one of those people. Naturally, being curious, I wanted to learn more about these technologies. I did what all of us do: a web search. And I found a myriad of resources, most of which were either too basic or too complex and filled with jargon. Moreover, they are entirely unstructured and I felt like I was picking up tiny pieces of information here and there, instead of learning in a structured, “builds on top of previous knowledge” way.
Since I could not find a decent non-technical resource that will allow me to learn about these technologies in a structured way, I decided to create one (in collaboration with Sergio from Your Coding Teacher).
This course will teach you everything you need to know about Bitcoin, Ethereum, Blockchain, DeFi, NFTs, etc. as a non-developer (i.e. you can understand everything without having a technical background).
All the course content is freely available and self-paced i.e. you can watch and read as per your leisure.
You will notice that some concepts are covered in multiple resources or sections. This redundancy is a feature of this course, not a bug. We deliberately looked for resources that demonstrated key concepts from different angles and at different levels of complexity to ensure the best possible learning experience for you.
Course Duration
| Module | Content Duration | Estimated time* |
| 1. Bitcoin | 18 hours | 3 weeks |
| 2. Ethereum and Smart Contracts | 10 hours | 2 weeks |
| 3. Web3 (Tokens, DApps, Oracles, IPFS, The Graph) | 11 hours | 2 weeks |
| 4. Decentralized Finance (DeFi) | 52 hours | 9 weeks |
| 5. Privacy Coins | 24 hours | 4 weeks |
| Total: | 115 hours | 20 weeks |
*assumes that you devote 6 hours per week to your studies.
Note: The content must be watched/read in the order presented. Each resource builds upon the information and concepts learnt in the previous resources.
Module 1: Bitcoin
Preliminaries
The best way to learn a thing is to know its history. Before you start exploring the internals of Bitcoin, you have to know the history and context under which it was created and what problem it is trying to solve.
| Resource | Topics Covered | Effort |
| The History and Evolution of Money | money, currency, barter, fiat, capitalism, history of money, trust, commodity money, paper money, currency printing, double spending problem, centralization, decentralization, motivation behind Bitcoin | 15 m |
Before we get into the nitty gritty details, we want you to get a broad idea of what Bitcoin is and the technology we’re dealing with.
| Resource | Topics Covered | Effort |
| What is Bitcoin and how does it work? | ledger, public key, private key, digital signature, hash functions, proof of work, blockchain, mining, block reward | 30 m |
There are a couple of technical ideas that you need to know to grasp how Bitcoin works. For example, hash functions are the basis for Public Key cryptography and Proof of work, some of the pillars of Bitcoin design. This is what we will cover now.
The content here might feel technical and intimidating, but it’s just there so you don’t find the words alien when they’re used later on. It’s okay if you don’t fully understand the topics at the moment.
| Resource | Topics Covered | Effort |
| Hash Functions 1. What is a cryptographic hash function 2. How hard is it to reverse a cryptographic hash? | hash function, digital signature, MD5, SHA-256, collision resistance | 20 m |
| Public key cryptography concepts 1. Summary video 2. What are Digital Signatures? | public key, private key, hashing, fingerprint, encryption, decryption, digital signature | 20 m |
Optional: Chapter 2 of The GNU Privacy Handbook
Basic Bitcoin
This section is mandatory.
After finishing this section, you’ll be able to understand the Bitcoin whitepaper.
| Resource | Topics Covered | Effort |
| The basic concepts of bitcoin | history of Bitcoin, getting bitcoin, price discovery, QR code, satoshi unit, transaction fee, mempool bitcoin exchange, Bitcoin ATM, private and public keys, bitcoin address, base58, 21 million total supply, confirmations, blockchain, miner, halving, mining incentives, coinbase transaction | 2 h |
| Consensus in a decentralized network 1. Bitcoin Blockchain Consensus 2. Disambiguating the word “Consensus” 3. Disambiguating the word “fork” 4. What is Nakamoto Consensus (Optional) | byzantine fault tolerance, consensus, Nakamoto Consensus | 40 m |
| Nodes 1. What is the role of nodes 2. Types of nodes and forks | node, role of nodes in the network, consensus, 51% attack, full node, light/SPV node, pruned full node, archival full node, mining nodes, coinbase transaction, staking nodes, authority nodes, masternodes, lightning nodes, hard fork, soft fork | 30 m |
| Proof of work (PoW) and Consensus 1. Byzantine Fault Tolerance 2. Proof of Work 3. What is a 51% Attack | proof of work, byzantine general’s problem, byzantine fault tolerance, nakamoto consensus, 51% or majority attack | 20 m |
| Bitcoin Wallets 1. What is a Bitcoin Wallet and types of bitcoin wallets? 2. Visual explanation of wallets | wallet, HD wallets, full nodes, SPV light wallets, hot wallet, web wallet, desktop wallet, mobile wallet, hardware wallet, cold storage wallet, paper wallet, brain wallet, multi-signature | 20 m |
| The Bitcoin Whitepaper 1. The full text 2. Explanation | whitepaper | 3 h |
Extending Bitcoin
Bitcoin is a living creature. Developers continue working on its codebase, introducing new features, improving the documentation, fixing bugs, etc.
A Bitcoin Improvement Proposal (BIP) is a design document for introducing new features or information to Bitcoin. Submitting a new BIP follows a rigorous process to ensure the highest level of quality.
| Resource | Topics Covered | Effort |
| 1. The BIP approval process 2. BIP list (for reference) | List of all BIPs with explanation and status, how to add a new BIP | 10 m |
However, Bitcoin can also be extended without altering its source code. Although it was designed as a “peer-to-peer version of electronic cash”, Bitcoin provides a number of properties that can be leveraged to create applications on top of it, known as Layer 2 solutions.
In this section we will explore some of the most notable examples.
Improving Bitcoin’s scalability
As we have seen in previous sections, a new block is mined every 10 minutes on average. These blocks have a size limit of 1 MB. These two facts limit the number of transactions that the network can handle per unit of time.
Multiple solutions have been proposed to solve this problem. Here we will cover some of them.
The Lightning Network is a protocol that tries to improve Bitcoin’s ability to quickly handle payments via routed payment channels.
| Resource | Topics Covered | Effort |
| Lightning Network 1. Video Introduction 2. Understanding the Bitcoin lightning network 3. (Optional) Understanding the Lightning Network Part I, Part II and Part III | payment channels, routed payment channels, lightning network, layer 2, multisig, hash time locked contracts (HTLCs), watchtowers | 2 h |
Other solutions have been proposed to solve the scalability problem:
- Although it is not its main purpose, Segwit is an upgrade to the Bitcoin protocol that helps improving Bitcoin’s scalability by effectively making transactions smaller and solving the malleability bug which enables the Lightning Network
- Increasing the block size, which resulted in multiple forks giving birth to Bitcoin Cash and Bitcoin Satoshi Vision.
- Schnorr signatures use a faster algorithm to create digital signatures and can combine signatures (from multisig transactions or from transactions with multiple inputs) effectively reducing the transaction size and improving the network capacity.
- Side chains are blockchains (separate from Bitcoins blockchain) that enable Bitcoin’s and other ledger assets to be transferred back and forth between multiple blockchains.
Most of these concepts will be covered in more detail in the upcoming sections.
Tracking assets in the real world (Optional)
Beyond its original use as a digital currency, Bitcoin transactions have been used in clever ways to keep track of assets outside of the blockchain. There are different methods to use transaction metadata to encode the ownership of an asset (a song, a painting, etc.) in the Bitcoin blockchain. These methods are referred to as Colored coins. A notable example is Omni Layer.
Advanced Bitcoin
This section contains advanced and somewhat technical resources for those wishing to go deeper.
Mandatory
| Resource | Topics Covered | Effort |
| Bitcoin Transactions (pre-Segwit) 1. Transactions in depth Part 1 2. Transactions in depth Part 2 | multiple inputs, multiple outputs, locking and unlocking transactions | 40 m |
| Segwit 1. Transaction Malleability 2. What is Segwit | segregated witness, transaction malleability | 25 m |
| The Script language | script programming language, p2pk, p2pkh, p2ms, p2sh | 1 h |
| More Segwit | segregated witness, transaction fee | 20 m |
| Merkle Trees 1. Merkle Roots and Merkle Trees 2. Merkle Proofs (first 3 m only) 3. (optional) Data corruption and Merkle trees 4. How SPV nodes use Merkle trees 5. How SPV nodes communicate with full nodes | merkle tree, merkle tree leaf, merkle root, merkle proof, nonce | 1.5 h |
Optional
| Resource | Topics Covered | Effort |
| Bloom Filters 1. What are bloom filters and why they exist 2. Bloom Filters and SPV nodes within the Bitcoin blockchain 3. Bloom Filters and SPV | bloom Filters, privacy | 30 m |
| Elliptic Curve Cryptography | elliptic curve cryptography | 15 m |
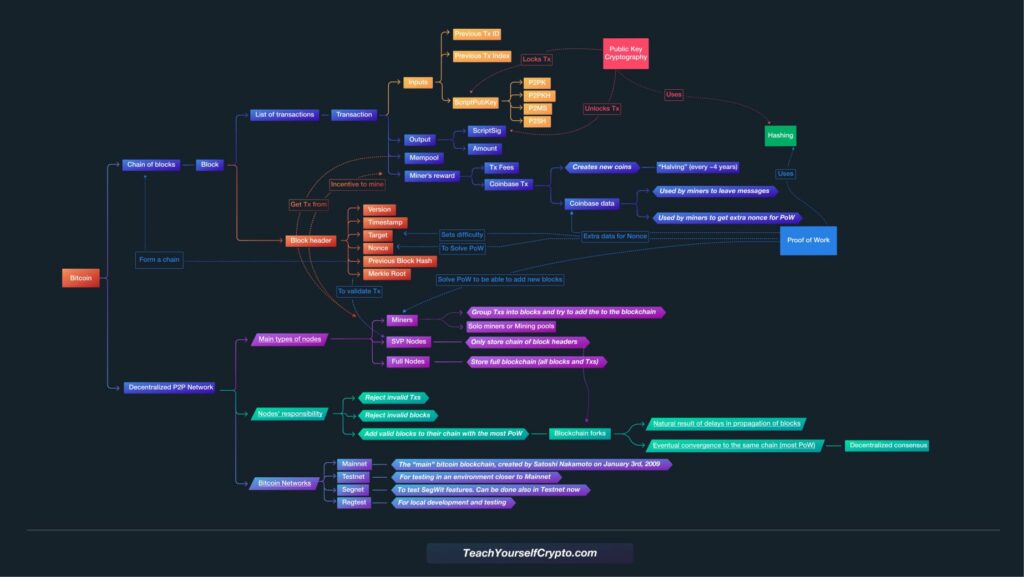
Bitcoin Mind Map
The Future of Bitcoin
Since Bitcoin is a decentralized project, there is no official roadmap to rely on. However, these topics are part of the community discussion and might become relevant in the future.
| Resource | Topics Covered | Effort |
| Quantum Computing Risks | risks of quantum computing in the future | 10 m |
| Hot Topics 1. Schnorr signatures 2. Taproot | privacy, scalability, smart contracts | 15 m |
Bitcoin FAQ
Bitcoin History and Culture
Optional reads to become familiar with the culture and history of Bitcoin
| Resource | Topics Covered |
| Bitcoin Auction: 10,000.00 BTC — Starting Bid 50.00 USD | In March 2010, user “SmokeTooMuch” auctioned 10,000 BTC for $50 (cumulatively), but no buyer was found. |
| The Story of The Bitcoin Pizza | On 22 May 2010, Laszlo Hanyecz made the first real-world transaction by buying two pizzas in Jacksonville, Florida, for 10,000 BTC |
| History of Bitcoin | A full chronological timeline of Bitcoin |
| The rise and fall of Mt. Gox | Story of the first Bitcoin exchange |
| The Long Road To SegWit: How Bitcoin’s Biggest Protocol Upgrade Became Reality | The history of Segwit |
| What is Bitcoin Cash (BCH)? | Bitcoin Cash |
| What is Bitcoin SV (BSV) | Bitcoin Satoshi Vison |
Module 2: Ethereum and Smart Contracts
Starters
| Resource | Topics covered | Effort |
| High level overview | A lighthearted introduction from the founder Vitalik Buterin himself | 2.5 h |
Preliminaries
Ethereum is a distributed, unbounded state machine. This section will give an overview of what a basic state machine looks like.
| Resource | Topics covered | Effort |
| Finite State Machines | finite state machines | 20 m |
Smart Contracts
| Resource | Topics covered | Effort |
| What is a Smart Contract? (Video) | smart contracts, trust, examples of smart contracts | 30 m |
The Ethereum Protocol
| Resource | Topics covered | Effort |
| What is Ethereum and how does it work? (Video) | Ethereum network, Externally owned accounts, contract accounts, ETH transactions, transaction structure, state, consensus, wei | 30 m |
| What is Gas and what role does it play? (Video) | gas, gas price, gas cost, gas limit, block gas limit, block size, infinite loops, turing completeness, EVM, gwei | 30 m |
| Mining Incentives 1. Block rewards and gas fees 2. Incentives on uncled blocks | block rewards, gas fees | 15 m |
| Transactions 1. UTXO vs Nonce Increments 2. Transactions in depth | account based blockchains, UTXO, EOA, Contract accounts, replay attacks | 20 m |
| Ethereum Virtual Machine (Optional, but recommended) | Ethereum Virtual Machine (EVM), nonce | 20 m |
Practical Exercises
Ethereum Improvement Proposals
Ethereum Improvement Proposals (EIPs) describe standards for the Ethereum platform, including core protocol specifications, client APIs, and contract standards. The full list of EIPs can be found at eips.ethereum.org.
| Resource | Topics covered | Effort |
| EIP 1559 1. What is EIP 1559 2. EIP 1559 from a miner’s perspective (Optional) | EIP, first price auction, EIP 1559, feecap, base fee, inclusion fee (miner tip), base fee burning, miner extracted value, EIP 3368 (rejected) | 15 m |
Ethereum 2.0
Ethereum 2.0 is a set of upgrades that aim to make the network more scalable, secure, and sustainable. At the time of this writing, the development is still in progress. These are the main technical ideas you need to know to understanding what the upgrade to Ethereum 2.0 represents.
| Resource | Topics covered | Effort |
| What is Ethereum 2.0, explained with timeline | proof of stake, validators, staking, beacon chain, sharding, casper protocol, eWASM | 25 m |
| Official docs (Optional) | official docs | |
| Proof of Stake 1. What is Proof of Stake 2. PoS vs PoW | proof of stake, staking, forging blocks, docking | 20 m |
| Sharding (Note: This video is general and not ETH specific, ignore the block size being represented in MB) | sharding, inter shard communication | 10 m |
Layer 2
Layer 2 is a collective term for solutions designed to help scale your application by handling transactions off the Ethereum mainnet (layer 1), while taking advantage of the robust decentralized security model of mainnet.
| Resource | Topics covered | Effort |
| What is Layer 2 Scaling? | rollups, plasma, channels, sidechains | 15 m |
Ethereum History and Culture
| Resource |
| The Prehistory |
| The History |
| The DAO Story 1. The DAO Hack and Smart Contracts on Ethereum 2. Ethereum Classic? 3. How the DAO Hack Changed Ethereum |
Is it fair to compare Bitcoin and Ethereum?
Module 3: Web3 (Tokens, DApps, Oracles, Filecoin and IPFS, The Graph)
Tokens
| Resource | Topics covered | Effort |
| The Ultimate Guide to Crypto Tokens | token, examples of tokens, fungible tokens, non-fungible tokens (NFTs), currency tokens, asset backed tokens, reward tokens, governance tokens, utility tokens, security tokens, equity tokens, token standards, interfaces, difference between token and cryptocurrency, Initial Coin Offerings (ICO) | 30 m |
| ERC 20 | ERC 20 Token Standard | 10 m |
| ERC 721 | ERC 721 Token Standard | 10 m |
| Art NFTs and Trading Platforms | Examples of NFTs with platforms where they are traded | 10 m |
Wrapped Tokens
| Resource | Topics covered | Effort |
| Wrapped Tokens 1. What are Wrapped Tokens 2. How token wrapping and unwrapping works | wrapped Tokens, custodian | 15 m |
| How to wrap Ethereum to wETH | wETH | 15 m |
Decentralized Applications (DApps)
| Resource | Topics covered | Effort |
| How apps work? | frontend and backend | 5 m |
| DApps 1. What is a DApp 2. Introduction to DApps | Decentralized Application (Dapp), benefits of DApps | 10 m |
| Exploring a DApp (Cryptokitties) 1. How to play Cryptokitties 2. Examining the Cryptokitties codebasae | Cryptokitties, Fungible and non-fungible assets, ERC-20, ERC-721, Cryptokitties codebase, Events | 30 Min |
| Find and explore more DApps | Practical Exercise |
Ethereum Name Service (ENS)
| Resource | Topics covered | Effort |
| What is Domain Name System (DNS) | domain name system | 10 m |
| Practical Exercise 1. Type this IP address into your browser: 40.114.177.156 You will land on DuckDuckGo, a privacy oriented search engine. You can always connect to websites by their IP addresses (however, some websites will reject connections coming this way for security reasons). The .com name is simply a DNS mapping to make things easy for humans to remember. 2. Register a domain name.Go to Namecheap and register a domain name for yourself. Register your FirstnameLastname.com. | 20 m | |
| Ethereum Name Service (ENS) 1. What is ENS? 2. ENS Architecture (optional) | ENS, registry, resolvers, namehash | 15 m |
| Register an ENS Domain | Practical Exercise | 15 m |
| ENS FAQ | controller, registrant, ownership, reverse record | 10 m |
Oracles and Chainlink
Oracles
| Resource | Topics covered | Effort |
| Oracles 1. What is an Oracle 2. Why do we need Oracles | Oracles, software and hardware oracles, deterministic blockchain, Decentralized Oracles, Chainlink basics, trusted execution environment | 20 m |
| The Oracle Problem 1. What is the Oracle problem? 2. Chainlink and the Oracle Problem | blockchain middleware, oracle problem, need for separate network, centralized oracle risks, need for decentralized oracles | 15 m |
Chainlink
| Resource | Topics covered | Effort |
| What is Chainlink | Chainlink, how chainlink works, requesting contract, chainlink service level agreement contract (CLA), reputation contract, order matching contract, aggregating contract, | 15 m |
| How does Chainlink work | The chainlkin protocol: Reputation contract, order matching contract, aggregating contract | 10 m |
| Tokenomics and use cases | Chainlink use cases, tokenomics Note: Some of the use cases will be more understandable after you complete the module on Decentralized Finance (DeFi) | 30 m |
| Chainlink factsheet | Chainlink, chainlink use cases, chainlink partners, network of oracles, threshold signatures, ERC677, chainlink tokenomics, total supply, initial token distribution, LockDeposit contract, Service Agreement (SA) model, mixicle, trusted computation framework (TCF), trusted execution environments (TEE), staking collateral, chainlink marketplaces, node reputation parameters Note: Mixicles will make more sense after you complete the module on Privacy Coins. | 30 m |
| ERC-677 Tokens (Technical/Optional) | Problems with ERC-20 tokens, EIP-150, call depth attack, ERC-223 tokens, ERC-777 tokens Note: Chainlink is an ERC-677 Token | 10 m |
Decentralized Autonomous Organizations (DAOs)
| Resource | Topics covered | Effort |
| What are DAOs 1. What is a DAO 2. Discussion on DAOs | decentralized autonomous organizations (DAOs) | 35 m |
| DAO voting tutorial | Example of voting on a DAO Note: The Snapshot platform is covered later in the DeFi section | 10 m |
Web 3.0 and Decentralization
Note: This is a different concept from semantic web, which is also sometimes called web 3.0.
| Resource | Topics covered | Effort |
| Web3 1. What is Web 3.0 2. Web2 vs Web3 | Web 1.0, Web 2.0, Web 3.0, Web 3.0 Foundation, web2 vs web3 | 15 m |
| The meaning of decentralization | Decentralization, Architectural (de)centralization, Architectural (de)centralization, Architectural (de)centralization, fault tolerance, attack resistance, collusion resistance | 20 m |
| The importance of Web3 and decentralization 1. Why decentralization matters 2. Why web3 matters | History of the internet, the importance of decentralization, the importance of web3 | 20 m |
Filecoin and the InterPlanetary File System (IPFS)
| Resource | Topics covered | Effort |
| What is IPFS | IPFS (Interplanetary File System), location based addressing, content based addressing, IPFS Objects, drawbacks, filecoin, applications, dtube | 10 m |
| What is Filecoin | Filecoin | 5 m |
| Tutorial: How to upload and access files on IPFS (First 3 minutes only) | How to use IPFS | 5 m |
| The IPFS Protocol (Ignore the command line demo and content on NAT) | HTTP vs IPFS, Content ID (CID), immutability, routing, distributed hash tables (DHT), bootstrapping, kademlia, Interplanetary Name Server (IPNS), deleting content | 25 m |
| Importance of decentralized storage (including the podcast) | Importance of decentralized storage on the internet, decentralized timestamping service | 45 m |
The Graph Protocol
This section is somewhat technical and it’s okay if you don’t fully understand it. The graph protocol is primarily of developer interest.
| What is a subgraph? The Graph protocol harvests data from the Ethereum blockchain and feeds it into its network of subgraphs. A subgraph is effectively an indexing service configured to seek out transaction data from a particular smart contract or set of smart contracts. A subgraph defines which data should be indexed and how they will be stored and queried. Once deployed, subgraphs could be queried by dApps to fetch blockchain data to power their frontend interfaces. In simple words, a subgraph is like a database. |
| Resource | Topics covered | Effort |
| What is The Graph 1. High level overview 2. The Graph explained | The Graph (GRT), Graph Protocol, indexing, querying, Google of blockchains, ingestion services, indexers, consumers, curators, delegators, fishermen, arbitrators | 20 m |
| What is an Application Programming interface (API) | API, API key, Software Development Kit (SDK) | 10 m |
| Why we need The Graph 1. Before and after The Graph (optional/technical) (Read until “How to create a Subgraph”) 2. How Does The Graph Fit Into DeFi and Web3 | Why do we need The Graph, GraphQL | 15 m |
| The Graph in Depth 1. Part 1 2. Part 2 (Ignore the math) | Full-Stack Decentralization, GRT Token use, Architecture, Protocol Roles, Service Discovery, Indexer Selection, Query Market, Conditional Micropayment, attestation, Indexer Staking, Curator Signaling, economic security, work token, indexer staking, thawing period, Sybil resistance mechanism, delegation, Curator Signaling, inflation reward, Proofs of Indexing, Subgraph Availability Oracle, Graph Explorer, Graph Name Service (GNS), subgraph manifest, subgraph composition, curation, WAVE Locks (work, attestation, verification, expiration), hash preimage, state channels, Query Verification, Single Attestation Disputes, Conflicting Attestation Disputes, Arbitrator, fishermen, The Graph Council Note: Some portions of this section will make more sense after you complete DeFi (more specifically, the content on bonding curves) | 1 h |
The Web3 Stack: Putting the Pieces Together
| Resource | Topics covered | Effort |
| The Architecture of a web 3.0 application (Don’t worry about the JSON-RPC stuff) | Web 2.0 backend and architecture, Web 3.0 backend and architecture, IPFS, Infura, Pinata, Swarm, querying the blockchain, The Graph, Polygon, Scaling L2 | 15 m |
Module 4: Decentralized Finance (DeFi)
Note: This module has a bit of the chicken and egg problem. The resources teaching DEXs will sometimes reference the lending protocols (Compound, AAVE) as examples, while the resources teaching lending protocols will occasionally reference the DEXs. In this situation, it’s okay to not understand everything right away – just make sure you mark what you don’t understand and come back when you’re done with the entire module once.
Other than that, this module is a lot of fun as it has a lot of real world applications. You’re going to have a good time!
The Traditional Banking System
| Resource | Topics covered | Effort |
| How the traditional financial system works (watch all videos) | Banks, banking, Fractional reserve banking, M0, M1, M2, bank note, check, reserve ratio, leverage, reserve bank (central bank), treasuries, open market operations, bank rate, fed funds rate, target rate, money supply, gold standard vs fiat, fed funds rate, discount rate, repo and reverse repo transactions, deposit insurance, LIBOR | 6 h |
What is DeFi
| Resource | Topics covered | Effort |
| Introduction to DeFi | Decentralized Finance (DeFi) | 30 m |
| Linking TradFi to DeFi | A lighthearted introduction by your course author | 45 m |
Stablecoins
| Resource | Topics covered | Effort |
| Preliminaries 1. Volatility 2. Liquidity 3. Collateral 4. Floating Rates and Fixed Rates (concept, comparison) 5. Pegged Currency | volatility, liquidity, collateral, floating rate, fixed rate, pegged currency, floating currency, crawling peg, clean float, Fixed vs Floating Exchange Rates (Arguments For and Against), Currency Peg | 40 m |
| What is a stablecoin and why we need them | Stablecoin, collateral peg, algorithmic peg, examples of stablecoins | 15 m |
| Types of stablecoins and comparison | stablecoin importance, collateralized stablecoins, real world collateral, crypto collateral, algorithmic stablecoins, USDT, USDT risks, USDC, BUSD, GUSD, DAI | 25 m |
| Tether (USDT) | Mastercoin, Realcoin, OMNI Layer Protocol, Tether | 10 m |
| MakerDao 1. What is Dai and MakerDAO 2. How to Setup a CDP Vault on MakerDAO 3. MakerDAO Mechanism Design | stablecoin, DAI, MKR, MakerDAO, collateralization ratio, interest, SAI, multi collateral DAI, black thursday liquidation event, Product demo, vault, collateralized debt position (CDP), liquidation ratio, liquidation fee, liquidation price, Dai Savings rate, stability fee, emergency shutdown | 1 h |
Decentralized Exchanges (DEXs)
| Resource | Topics covered | Effort |
| Preliminaries 1. Shares/stocks 2. Financial instrument 3. Order Book 4. Markets 5. Exchanges 6. Broker-Dealer 7. Market Maker 8. Market Index 9. Long and Short 10. Leverage 11. Margin 12. Counterparty and counterparty risk 13. Trade Slippage | stocks, financial instruments, contract, financial assets, financial liabilities, equity instruments, order books, markets, financial market, exchange, trading, brokers, dealers, broker-dealer, market maker, bid, ask, spread, market index, long trades, short trades, leverage, margin trading, counterparty, counterparty risk, trading slippage | 1.5 h |
| What is a Decentralized Exchange (DEX) | DEX, Centralized Exchanges (CEX), Automated Market Makers (AMM), how DEXs work, risks | 10 m |
| How Layer 1 order book DEXs work | order book based DEXs, 0x Protocol, 0x Relayer, Atomic Swap, wrapping | 15 m |
| Atomic Swap | Atomic Swaps | 10 m |
| Liquidity Pools and Automated Market Makers (AMM) 1. What is an AMM 2. What is a liquidity pool 3. How do liquidity pools work 4. AMM math, concept, and need 5. Summary | automated market maker (AMM), constant product market maker algorithm, order book exchanges, liquidity pools, slippage, liquidity providers, impermanent loss, arbitrages (arbs) | 1 h |
| Impermanent Loss | impermanent loss | 10 m |
| Rug Pulls | rug pulls with examples | 10 m |
| Uniswap 1. The story of Uniswap 2. How Uniswap Works 3. Uniswap v3 (Note: Video has an error at 6:10 – should be 3000 buy and 4000 sell) | Uniswap, History of Uniswap, UNI token (governance token), Sushi swap, Uniswap v1 vs v2 vs v3 comparison, concentrated liquidity, concentration multiplier, active liquidity, NFT liquidity token, LP token, licensing | 1 h |
| Slippage 1. What is slippage 2. Frontrunning and sandwich attacks | slippage, sandwich attack, frontrunning, tolerance | 40 m |
| Balancer | Balancer | 10 m |
| Curve Finance 1. What is Curve Finance 2. How the math behind Curve Finance Works | Curve Finance | 25 m |
| Bancor 1. What is Bancor and BNT 2. How does the Impermanent Loss Insurance Work (Bancor v2.1) 3. More on Impermanent Loss Insurance and Single Sided Liquidity | Bancor, BNT token, liquidity protection, impermanent loss insurance, single side liquidity, Bancor Vortex, product demo | 35 m |
| Token Bonding Curves 1. Token Bonding Curves and Token Valuation 2. Token Bonding Curve Algorithms for Autonomous Market Makers (DEX) (Skip the math portion if you don’t understand it, the important part is the concept) | Token Bonding Curves, buy curve, sell curve, properties of token bonding curves, valuation, risk mitigation, bonding curve functions, linear functions, power functions, logarithmic functions, sigmoid functions, calculating price | 2 h |
| dYdX 1. What is dYdX 2. How dYdX works and product demo | dYdX, DYDX token, perpetuals, layer 2 vs layer 1, starkware, stark rollups, zero knowledge proof, optimistic rollup, dYdX product demo | 40 m |
| Loopring | Loopring, zk rollups, merkle trees, how Loopring works, LRC token, LRC tokenomics, slashing, trading fees, loopring DAO, LRC ICO, LEAF | 25 m |
Dex Aggregators
| Resource | Topics covered | Effort |
| What is a DEX Aggregator | DEX Aggregators | 5 m |
| 1inch 1. What is 1inch and how it works 2. How to use 1inch | 1inch, 1inch v2, 1inch Token, price impact fee, product demo | 20 m |
Decentralized Lending and Borrowing
| Resource | Topics covered | Effort |
| Preliminaries 1. Money market 2. Peer to Peer Lending 3. Annual Percentage Rate (APR) 4. Total value Locked (TVL) | money market, treasury bills, certificate of deposit (CDs), commercial paper (CP), discount to par, P2P lending, annual percentage rate (APR), effective APR, daily periodic rate, total value locked (TVL) | 15 m |
| Introduction to decentralized lending and borrowing | DeFi lending, Compound, Aave | 15 m |
| Compound Finance 1. What is Compound and what are cTokens 2. How to use Compound Finance 3. Compound Protocol Math (optional) 4. Governance and vision (starts at 22:30) | supplying assets, borrowing, collateral factor, cTokens, types of cTokens, mint functions, compound v2, cETH, cDai, cUSDC, exchange rate, product demo, overcollateralization, forced liquidation, exchange rate math, governance | 2.5 h |
| Homework: Deposit some test ether into compound, and go to etherscan for your address and check whether you received your cETH. In general, you want to play around with all the protocols in this module, using either mainnet ether or test ether. | ||
| Aave 1. What is Aave 2. Aave concepts and how to borrow and lend on Aave 3. Aave Tutorials (resource 1, resource 2) 4. Flash Loans (resource 1, resource 2) 5. How to use flash loans with code (optional) | Aave protocol, AAVE token, history, ETHLend, overcollateralization, liquidation threshold, leveraged lending, aTokens, flash loans, total value locked, aavenomics, shortfall event, AAVE v2, aavengers, variable and stable interest rate loans, utilization rate, swapping collateral, aave safety module, risks, repayment with collateral, Aave markets, product demo, flash loans, atomic transactions, flash loan use cases, arbitrage, self-liquidation, PancakeBunny flash loan attack, how to use flash loans (coding tutorial) [Notes for the Flash loans videos: Resource 1: video assumes the loan was in USD stablecoin in the initial example Resource 2: mention Polygons, those curious can learn more about Polygon here] | 1.5 h |
Decentralized Derivatives
| Resource | Topics covered | Effort |
| Preliminaries 1. Derivatives 2. Hedging 3. Swaps 4. Futures 5. Options – calls and puts | forwards, futures, options, derivatives, swaps, exchange, over the counter (OTC), leverage, counterparty risk, hedging, swaps, fixed and variable rates of interest, futures, forwards, future curves, options, puts, calls, option strategies | 1 h |
| What are decentralized derivatives? | decentralized derivatives | 15 m |
| Synthetix 1. What is Synthetix and product demo 2. How does Synthetix work? | Synthetix, synthetic assets, risks, SNX, synths, synthetic equities, layer 2 with Optimism, debt pool | 1.5 h |
| Introduction to DeFi Option Protocols | options, european options, american options, Hegic, Opium, Opyn | 40 m |
| Opyn 1. What is Opyn and how it works 2. How to use Opyn | Opyn, convexity protocol, oTokens, Opyn v1, Opyn v2, gamma portal, governance mechanisms, incentives, settlement, product demo | 30 m |
Decentralized Asset Management
| Resource | Topics covered | Effort |
| Preliminaries 1. Market Index 2. Fund Management or Asset Management (resource 1, resource 2) 3. Mutual Funds 4. Hedge Funds 5. Index Funds | stock market index, dow, S&P 500, Nasdaq fund management, asset management, exchange traded fund (ETF), mutual funds, hedge funds, strategies, compensation, hedge fund structure, index funds | 50 m |
| Set Protocol / TokenSets 1. What is Set Protocol 2. More on Set Protocol 3. Even more on Set Protocol 4. How to choose a Set 5. What is the difference between Social Trading and Robo Sets? 6. DeFi Pulse Index 7. How to Buy the DeFi Pulse Index | Set Protocol, TokenSets, user roles, use cases Robo Sets, Social Trader Sets, DeFi Pulse, product demo, streaming fee | 1.5 h |
DeFi Dashboards
| Resource | Topics covered | Effort |
| Zapper 1. What is Zapper 2. How to use Zapper | Zapper, risks, product demo | 30 m |
| Instadapp 1. What is Instadapp 2. What services does Instadapp provide 3. Need for InstaDApp 4. Instadapp tutorial | Instadapp, DeFi Smart Accounts (DSAs), DeFi Smart Layer (DSL), INST token, product demo | 30 m |
Yield Farming
| Resource | Topics covered | Effort |
| Preliminaries 1. Yield | bonds, yield | 5 m |
| Concept of Yield Farming | yield farming, liquidity mining | 20 m |
| Yearn Finance 1. What is Yearn Finance 2. What are Yearn Vaults 3. How to use Yearn finance | Yearn finance, YFI, liquidity mining, vaults, Yearn vaults, vault strategies, YETH vault, risks, product demo | 30 m |
| Yield Farming (Video has an error at 8:30, should be “inflationary in nature”) | yield farming strategies, leveraged lending and borrowing, staking, liquidity providers, redistribution fees, safemoon, risks | 15 m |
| Degen Yield Farming | degen yield farming, Rugdoc, VFat | 15 m |
Decentralized Payments
Although decentralized payments can already be done with Bitcoin and Ethereum directly, the aim here is to make them faster, cheaper, and to add additional features like payment streams, conditional transfers, and more.
| Resource | Topics covered | Effort |
| Preliminaries 1. Blockchain Bridge 2. Sidechain (plasma section is optional) 3. Block Explorer 4. On and Off Ramps | blockchain bridge, centralized and decentralized bridges, sidechain, issues with sidechains, plasma, block explorer, On and Off Ramps | 50 m |
| xDai | xDai, STAKE | 25 m |
| Sablier 1. What is Sablier 2. Use cases and tutorial | Sablier, payment streams, streaming money | 25 m |
Algorithmic Stablecoins
| Resource | Topics covered | Effort |
| Preliminaries 1. PID Controller | PID Controller | 5 m |
| What are Algorithmic Stablecoins | Algorithmic Stablecoins, rebase contract, stabilizer contract, ampeforth, death loop, risks, RAI, FEI, FRAX | 10 m |
| Stablecoin Algorithms | Rebase, debase, supply volatility, Seigniorage supply, Empty Set Dollar Coin (ESD), Basis Cash, Titan, Iron Finance | 10 m |
| Iron Finance (and it’s collapse) | The collapse of Iron Finance, IRON, TITAN, STEEL, Target Collateral Ratio (TCR), Effective Collateral Ratio (ECR) | 15 m |
| Frax 1. What is Frax 2. The economics of Frax | FRAX, FXS, veFXS, staking, dual token mechanism, FRAX v2, collateral ratio, minting FRAX, C-ratio update, PID controller | 35 m |
| Olympus | OlympusDAO, OHM, (3,3), Reserve Control Protocol, Treasury, Prisoner’s Dilemma, Floor Price, risks | 15 m |
| Magic Internet Money | Magic Internet Money (MIM), Abracadabra Money, SPELL, sSPELL, yDai, Popsicle Finance, ICE, nICE, Anyswap, Wonderland Money, TIME | 25 m |
Decentralized Prediction Markets
| Resource | Topics covered | Effort |
| Preliminaries 1. Prediction Markets | Prediction Markets, price signals and forecasting, Iowa Electronic Market, The Hollywood Stock Exchange | 10 m |
| What are Decentralized Prediction Markets | Decentralized Prediction Markets, bitcoin hivemind, augur, omen, delphy, polymarket, ftx exchange | 15 m |
| Why we need Decentralized Prediction Markets | Limitations of centralized prediction markets | 5 m |
| Augur 1. What is Augur 2. Overview and how to use Augur (first half only) [bad audio, email us if you find something better] | Augur, REP, market creation, resolution rource, Augur v2, invalid market, product demo | 25 m |
| Omen 1. What is Omen 2. More on Omen 3. How to use Omen | Omen, Realitio, arbitration, dxDAO, product demo, xDai, Scalar market | 30 m |
Decentralized Lotteries
| Resource | Topics covered | Effort |
| Preliminaries 1. How lotteries work | lotteries, how lotteries work | 10 m |
| PoolTogether 1. Overview of PoolTogether 2. What is PoolTogether 3. How to use PoolTogether | PoolTogether, Pools, POOL token, no loss lotteries, withdraw penalty, product demo | 20 m |
Decentralized Governance (DeGov)
| Resource | Topics covered | Effort |
| What is Decentralized Governance | governance in traditional public companies, chain governance, Bitcoin governance, forks, tezos governance, governance representatives | 25 m |
| Understanding Decentralized Autonomous Organizations (DAOs) | Decentralized Autonomous Organizations (DAO), The DAO hack, The DAO bailout, ETH Classic, MakerDAO, potential of DAOs | 25 m |
| Real world potential of DAOs | potential of DAOs, DAO structures | 20 m |
| DAO Treasury and Token Management | DAO treasury management, UMA range token, DAO security | 20 m |
| What gives governance tokens value | governance tokens, crypto governance model vs board of directors model, governance as a model | 20 m |
| Aragon 1. What is Aragon 2. How to build a DAO with Aragon | Aragon, ANT, Aragon Agent, product demo | 15 m |
| Snapshot 1. What is Snapshot 2. How to use Snapshot | Snapshot, use cases, how to vote using snapshot | 10 m |
| Flaws in coin governance and potential solutions | need for DeGov, DeGov issues and dangers, plutocracy, vote delegation, vote buying, bribes, tragedy of the commons, unbundling profit sharing from governance, protections and workarounds, potential solutions, limited governance, un-governance, time delay mechanisms, fork friendliness, non-coin-driven governance, proof of personhood, proof of participation, futarchy | 60 m |
Decentralized Insurance (with Nexus Mutual)
| Resource | Topics covered | Effort |
| Preliminaries 1. What is Insurance? 2. How do insurance companies make money 3. Smart contract risk | Insurance, aims of insurance, types of Insurance, smart contract risk, smart contract audits | 20 m |
| What is Decentralized Insurance | decentralized insurance | 20 m |
| Economics of the Insurance Industry and introduction to Nexus Mutual | Economics of Insurance Industry, inefficiencies, information asymmetry, warren buffet halo, signalling, economics of moral hazards, copayment, PA relationship, law of large numbers, tail risks, risks in DeFi, DAO hack, Pokadot parity multi-sig freeze, YAM finance governance token rebase contract, liquidation in Maker’s vaults, bZx smart contract exploit, internal and external techinical risks, economic incentive risks, quantifying risks, Nexus Mutual, insurance cover buyers, risk assessors, claim assessors, NXM, staking NXM, WNXM, Etherisc, reinsurance | 1.5 h |
| The Economics of Nexus Mutual | How Nexus Mutual works, functions of NXM tokens, yinsure, governance decision making, governance resolution, advisory board powers, emergency pauses, 12h cool off period, NXM bonding curve, Minimum Capital Requirement (MCR), capital pool, dynamic capital flow, MCR Ratio, NXM supply, gearing factor | 1.5 h |
| How to buy Insurance with Nexus Mutual | NXM tokenomics, buying cover, KYC, Nexus Mutual legal structure, WNXM, product demo, risks | 1 h |
Multi-Chain Protocols and Bridges
| Resource | Topics covered | Effort |
| Ren Project 1. What is the Ren Protocol and renBTC 2. How to swap BTC for renBTC | Ren Protocol, RenVM, RenBTC, dark nodes, Sharmir’s Secret Sharing Algorithm, WBTC, BitGo | 15 m |
| ThorChain 1. How does ThorChain work 2. How to use ThorSwap | native assets, thorchain, Tendermint, Cosmos SDK, Threshold Signature Scheme (TSS), instaswap, bepswap, single-chain chaos network (SCCM), multi-chain chaos network (MCCM), Tendermint BFT, THORnode, BIfrost, witness transactions, inbound vaults, outbound vaults, RUNE token, bonding, churning, sharded vaults, incentive pendulum, dynamic slip based fee, thorswap, impermanent loss protection, product demo | 30 m |
| Binance Bridge | Binance smart chian, binance bridge, binance chain wallet | 5 m |
| Anyswap | AnySwap, ANY, product demo | 10 m |
| Terra 1. What is Terra, UST, and LUNA 2. Terra Station Tutorial (how to buy and stake Terra and Luna) | Terra, UST, LUNA, Terra Blockchain, Andhor protocol, Mirror protocol, mAssets, Chai, Terra Station, delegated proof of stake | 25 m |
Decentralized Capital Raising
| Resource | Topics covered | Effort |
| Initial Coin Offering (ICO) | Initial Coin Offering (ICO), risks | 10 m |
| Security Token Offering (STO) | Security Token Offering (STO), utility tokens, security tokens, regulation | 15 m |
| Initial Exchange Offering (IEO) | Initial Exchange Offering (IEO) | 10 m |
| Initial DEX offering (IDO) | Initial DEX offering (IDO) | 5 m |
| Bonding Curve Offering (BCO) [skip the parts about Onomy] | Bonding Curve Offerings (BCO) | 5 m |
| Liquidity Bootstrapping Pool (IBP) | Balancer, liquidity bootstrapping pools (LBP), IDO vs IEO, uniswap IDOs, Mesa IDOs, Hegic IBCO, how LBPs work, LBP examples | 40 m |
| Initial Farm Offering (IFO) | Initial Farm Offering (IFO) | 5 m |
Miscellaneous topics
| Resource | Topics covered | Effort |
| Total Value Locked (TVL) 1. TVL meaning in different DeFi Product Categories 2. Double counting problem with TVL | total value locked, double counting | 20 m |
| Airdrops | airdrop | 5 m |
| Tokenomics | tokenomics, pre-mining, fair launch, circulating supply, total token supply, max supply, inflationary token model, deflationary token model | 20 m |
| Miner Extractable Value (MEV) 1. Understanding Mempool & Miner Extractable Value 2. Frontrunning, MEV, consensus Instability 3. Miner Extractable Value (MEV) | Miner Extracted Value, time bandit attack, mempool | 2 h |
| Risks of DeFi | smart contract bugs, phishing, oracle failure, admin key risk, liquidity crisis, governance failure, de-pegging risk | 10 m |
The past and the future
| Resource | Topics covered | Effort |
| Brief history of DeFi | history of DeFi with timeline | 20 m |
| The Future of DeFi | future of DeFi | 10 m |
Module 5: Privacy Coins
Privacy on the Bitcoin Network
| Resource | Topics Covered | Effort |
| Why we need Privacy 1. Why financial privacy matters 2. Bitcoin’s biggest weakness | Privacy, drawbacks of Bitcoin, CoinJoin, Taproot, Schnorr signatures | 15 m |
| How to Get More Privacy on Bitcoin Transactions 1. Increasing privacy on Bitcoin Transactions 2. Things to keep in mind | Bitcoin Privacy | 10 m |
| CoinJoin 1. What is CoinJoin 2. Drawbacks of CoinJoin | CoinJoin, fungibility, traceability, anonymity sets, centralized mixing services, zero link protocol, cash shuffle algorithm, Mimblewimble, CoinJoin drawbacks, financial privacy | 20 m |
| Blacklisted/tainted coins 1. Blacklisted Vs Whitelisted Crypto 2. Blacklists, Taint, and Wallet Fingerprinting | Pseudonymity, Chainalysis, blacklisted or tainted coins, whitelisted coins, Blacklists, Taint, and Wallet Fingerprinting, Dandelion routing Note: Just because a chainanalysis company claims something, does not mean they have that ability. | 30 m |
| Bitcoin censorship and blacklists in practice 1. Bitcoin’s Fungibility Graveyard 2. CoinJoin Flagging | Examples of censorship due to lack of privacy and fungibility, Examples of censorship of people who want more privacy | 20 m |
| Bitcoin censorship potential and miners centralization 1. CPU, GPU, and ASIC mining (Ignore the second half that talks about Pahla) 2. Bitcoin’s ASIC problem 3. How could regulators successfully introduce Bitcoin censorship and other dystopias | CPU mining, GPU mining, ASIC mining, Bitcoin ASIC problem, miner centralization, Blockseer, censorship potential, Monero | 45 m |
| Workaround solutions (for reference) | Roundabout ways to get more privacy on a public ledger | 10 m |
Monero
Basic Monero
| Resource | Topics Covered | Effort |
| What is Monero 1. What is Monero (XMR) 2. Monero Explained | Monero, obfuscated public ledger, fungibility, ring signatures, public view key, private view key, public spend key, private spend key, stealth address, key image, RingCT | 15 m |
| How Monero Works (Monero Privacy Technologies) 1. Stealth Addresses 2. Ring Signatures 3. Ring Confidential Transactions (RingCT) | Stealth addresses, ring signatures, key images, Ring Confidential Transactions (RingCT) Note: Kovri is abandoned. It is partially replaced by i2p-zero, and by Dandelion which is discussed in later resources. | 10 m |
| Monero Addresses 1. Standard or Primary Addresses 2. Subaddresses 3. Integrated Addresses (Ignore the sections on math, data structures, and how to generate the addresses) | Standard or Primary Address (starts with a 4), Subaddresses (starts with an 8), Integrated Addresses, use cases, Payment ID/Memo | 15 m |
| Monero Key Types | Private View Key, Private Spend Key, Transaction Key | 5 m |
Stealth Addresses (Receiver’s Privacy)
The addresses mentioned above are converted into one-time stealth addresses by the sender’s wallet to protect the receiver’s privacy on the blockchain. This is a consensus rule, and transactions that do not use one-time stealth addresses are rejected by the network.
| Resource | Topics Covered | Effort |
| One-Time Stealth Addresses (Receiver Privacy) | Stealth address, burning address | 5 m |
Ring Signatures (Sender’s Privacy)
| Resource | Topics Covered | Effort |
| Basic Overview Ring Signatures | Ring Signatures | 5 m |
| Ring Signatures in Monero (Transcript) | Ring Signatures, key images, double spend protection, linkability, traceability, history of ring signatures, zero mixin (ring size 1), consensus enforcement, mandatory privacy, ringsize history, distinguishability, heuristics, privacy trade-offs, Zcash | 50 m |
Ring Confidential Transactions (RingCT) (Transaction Amount Privacy)
| Resource | Topics Covered | Effort |
| Zero Knowledge Proof (ZKP) | Zero Knowledge Proof (ZKP), interactive and non-interactive proofs, zk-SNARKS | 10 m |
| Pedersen commitment | Cryptographic Commitments, Pedersen commitment, homomorphic property | 10 m |
| Ring Confidential Transactions (RingCT) 1. What is RingCT 2. More on RingCT 3. How does RingCT work | RingCT, key image, Pedersen commitment, range proofs, transparent coinbase | 20 m |
| Bulletproofs 1. What are Bulletproofs 2. Range proofs and Bulletproofs 3. Bulletproofs in Monero 4. Bulletproofs+ in Monero | Range Proofs, Bulletproofs, Bulletproofs+ | 30 m |
Network Level Privacy (Optional)
| Resource | Topics Covered | Effort |
| Dandelion++ 1. Dandelion++ 2. Dandelion protocol and onion routing 3. Dandelion and Dandelion++ | Dandelion, Dandelion++, Spy Attacks, pros and cons, flooding, basic flooding, randomized flooding (diffusion), diffusion by proxy, stem phase, fluff phase, epochs, fail-safe mechanism, black-hole attacks Note: Dandelion++ is live. | 45 m |
Monero Coinomics
| Resource | Topics Covered | Effort |
| Monero as money (Ignore the math) | Money printing, pandemic economy, inflation, digital scarcity, elliptic curve cryptography, network security, fungibility | 1 h |
| Tail Emission | Network security, Tail Emission | 5 m |
| The infinite supply question | Infinite supply and inflation | 10 m |
Dynamic Block Size and Transaction Fees
| Resource | Topics Covered | Effort |
| Dynamic block sizes | Scaling, dynamic block size, spam attacks, fee markets | 5 m |
| Transaction Fees | transaction fee, dynamic fee algorithm, base reward, penalty | 10 m |
Supply Verification
| Resource | Topics Covered | Effort |
| How to fully audit the entirety of Monero’s supply and reliance on sound cryptography | How to fully audit the entirety of Monero’s supply, reliance on the soundness of the cryptography used | 5 m |
| Problems with supply auditability in Privacy Enhancing Cryptocurrencies (Article, Video) | Supply Auditability, problems with supply auditability on privacy enhancing cryptocurrencies, ElGamal commitments vs Pedersen Commitments | 40 m |
ASIC Resistance and Miner Decentralization
| Resource | Topics Covered | Effort |
| CryptoNight mining algorithm (Ignore the math) | CryptoNight, failure to resist ASICs | 5 m |
| RandomX mining algorithm (Ignore the math) | RandomX, CPU-only mining | 5 m |
| ASIC-Resistant Proof of Work and road to RandomX in Monero (Transcript) (Don’t worry if you don’t understand everything.) | ASIC-Resistant Proof of Work, RandomJS, CryptoNight/R, RandomX, why GPU resistance Note: RandomX is live. | 40 m |
Vulnerabilities and Potential Attacks
| Resource | Topics Covered | Effort |
| 0 decoy (Transcript) | 0-Decoy Attack/Analysis, Chain Reactions | 20 m |
| Key image reuse attack (Chain Splits) 1. How Monero protects against double spend attacks 2. Chain Splits (Key Image Reuse Attack (Transcript) | Key Images, Double spend prevention with key images, chain splits, tag, fork | 30 m |
| Input Selection Algorithm (Transcript) | Input Selection Algorithm, problems with true randomness | 15 m |
| Unusual Ringsizes (Transcript) | Unusual Ringsizes | 15 m |
| Remote Nodes (Transcript) | Attacks from Remote Node | 25 m |
| Timing Attacks (Transcript) | Timing Attacks, 10 confirmation requirement | 20 m |
| Poisoned Outputs (EAE Attack) (Transcript) | Poisoned Outputs (Eve Alice Eve Attack), marked money, probabilistic models, future of ring signatures for privacy on Monero | 30 m |
| Public Mining Pools 1. What is Churning 2. Public Mining Pools data leaks (Transcript) | Churning, Public Mining Pools, Payout transactions | 20 m |
| Miscellaneous (Transcript) (Optional) | interesting Q&A | 50 m |
| Input/Output Metadata (Transcript) | Input/Output Metadata, metadata analysis | 20 m |
| Blockchain Explorer OpSec (Transcript) | Blockchain Explorer OpSec | 10 m |
| Subaddress Association (Janus Attack) 1. Advisory note for users making use of subaddresses 2. Subaddress Association (Janus Attack) (Transcript) | Subaddress Association, Janus Attack | 25 m |
History and Culture
Miscellaneous
| Resource | Topics Covered | Effort |
| Monero vs BTC 1. Monero vs BTC 2. Growing Adoption | A lighthearted podcast with your author, adoption and growth compared | 1.5 h |
| Why fungibility matters | Why Fungibility Matters | 15 m |
| Dispelling Monero FUD | Addressing common concerns regarding Monero | 10 m |
Zcash
Introduction to Zcash
| Resource | Topics Covered | Effort |
| Intro to Zcash and Comparison to Bitcoin | Zcash, ZEC, zerocoin, Electric Coin Company, Zcash Foundation, 21 million total supply, Equihash, Zcash transaction, shielded and transparent addresses | 15 m |
| Zcash 101 (from the Electric Coin Company) | what is Zcash, resources to use Zcash, origin of Zcash, transparent and shielded addresses, viewing keys, multi-party computation, sprout, sapling, halo, trusted setup, zero knowledge proofs, halvening, regulation and compliance, history and roadmap (Nov 2020), Zcash foundation, project funding, founder’s reward, devfund, importance of financial privacy, interesting QA | 1 h |
| Zcash profile | History, roadmap, contributors, advisors, tokenomics, technology, governance, regulation | 25 m |
How Zcash Works
| Resource | Topics Covered | Effort |
| Anatomy of A Zcash Transaction | Zero knowledge proofs, t-address, z-address, Transparent Value Pool (TVP), transferring funds between different types of addresses | 5 m |
| What are zk-SNARKs? | Zero-Knowledge Succinct Non-Interactive Argument of Knowledge Proofs (zkSNARKs), Rank 1 Constraint System (R1CS), Quadratic Arithmetic Program (QAP) | 15 m |
| How Transactions Between Shielded Addresses Work | Notes, nullifier set, zero-knowledge proofs Note: The idea behind the nullifier set is similar to the idea of key images that you have learned about in the Monero section: it is a way of marking the notes as used to prevent double spending (once used, they become null). | 7 m |
| The Encrypted Memo Field | encrypted memo field, use cases | 7 m |
| Viewing Keys | viewing keys, payment disclosure, splitting viewing authority and spending authority | 3 m |
Zcash Founders’ Reward and DevFund
| Resource | Topics Covered | Effort |
| Funding, Incentives, and Governance | Zcash supply, 21 million coins, 10% of total supply to founders, 20% tax in miner’s reward for the first 4 years, Zcash company, Zcash foundation | 5 m |
| A Look at the Zcash Dev Fund Process – Josh Cincinnati (Executive Director of the Zcash Foundation) | History of Zcash dev fund process, Zcash Company, Zcash Foundation, Electric Coin Company, Y cash (z cash first fork), Zcash trademark ownership, involvement of Zcash community | 20 m |
| Zcash Development Funding | From November 2020, Zcash dev fund: Electric Coin Company, Zcash Foundation and Major Grants Review Committee (MGRC) | 1 m |
| Reaching consensus | New Zcash development fund | 10 m |
Equihash
| Resource | Topics Covered | Effort |
| Migrating to Equihash | Why Equihash, what changes, how to mine Zcash | 3 m |
| Understanding the Generalized Birthday Problem | Birthday paradox, 23 people in a room 50% probability of at least 2 of them having the same birthday, combinations, permutations, exponentials | 5 m |
| How does Equihash work? | Origin of the Equihash algorithm, Equihash’s goal, how does Equihash work?, the resolution algorithm, the end of equihash ASIC resistance, algorithm characteristics, cryptocurrencies using the Equihash algorithm | 10 m |
| Zcash Company Statement on ASICs | ASIC mining equipment, ASIC-resistance research, Overwinter, Sapling | 3 m |
Zcash Trusted Setup
The zk-proofs you have just seen require a one-time operation to initialize the algorithm, known as the trusted setup. This is an extremely important process, because if someone manages to get access to the secret generated during this setup, they could cheat the network: emit malicious transactions that would be accepted by the miners.
This process took place twice for Zcash, giving birth to two versions known as Sprout and Sapling. Zcash is currently working on Halo, based on a different approach that does not require an initial setup.
| Resource | Topics Covered | Effort |
| Zcash ceremony | Initial Zcash trusted ceremony | 5 m |
| Trusted setup | Trusted setup and why it’s needed | 5 m |
| What is Secure Multiparty Computation (SMC)? | Secure Multiparty Computation (SMC), Fully Homomorphic Encryption (FHE) | 8 m |
Double Spend Protection (Zero-Knowledge Proofs, zk-SNARKs, and Turnstiles)
| Resource | Topics Covered | Effort |
| Zero Knowledge Proofs, Zcash, Sprout, Sapling & zkSnarks (Note: Video starts at the 11 minute mark. Watch until 48:00.) | Zk-proofs, Zero-Knowledge Succinct Non-Interactive Argument of Knowledge Proofs (zkSNARKs), commitment schemes, commitment trapdoor, Zcash Sprout, Transparent value pool, Shielded value pool, transaction validation, double spending protection, payment address, incoming viewing key, full viewing key, proof authorizing key, expanded spend key | 40 m |
| Turnstile | turnstiles, transparent value pool, Sprout value pool, Sapling value pool, consensus rules in case pool becomes negative due to counterfeiting | 5 m |
| Zcash Sprout Shielded Pool Counterfeiting Vulnerability 1. Disclosure by Zcash team 2. Analysis by Monero devs | Discussion around the counterfeiting vulnerability in Zcash (generation of false proofs), BCTV14 vulnerability, Parno15, Fuchsbauer17, BBFR14, ADSNARK, PGHR13, BGG17, Groth16, Zcash turnstile, problems with turnstiles | 50 m |
If you want to learn more about zk-SNARKs and the math behind them, check out this 8 part series by the ECC. (This is optional).
History and Culture
| Resource | Topics Covered | Effort |
| History and future of Zcash | Zooko Wilcox, history of Zcash, privacy, future of web3, what is Zcash, Electric Coin Company, the trusted setup process, the setup ceremony, Zcash technical challenges, Zcash counterfeit vulnerability, why having dev funds, history of privacy on the internet, crypto protecting users like HTTPs, what’s more important than privacy, continuous improvements vs stability, Zcash shielded assets, crypto memos, Zcash in the future, halo, solving the blockchain scalability problem | 1 h |
| History of zk-SNARKs in Zcash (Ignore the math) | Sprout, trusted setup, BCTV14, BCTV14 flaw, structured reference string, Slow prover, Groth16, Sapling, recursive proof composition without a trusted setup, polynomial IOP (interactive oracle proof), Halo, Halo 2, Sinsemilla | 25 m |
Miscellaneous Resources
| Resource | Topics Covered | Effort |
| User Defined Assets (UDAs) | User Defined Asset (UDA), why privacy is important, effect of privacy on fungibility, front running, bridge smart contract blockchains with Zcash, stablecoins | 35 m |
Feedback
We would love to hear your feedback and any product improvement suggestions you have for us. Please send us an email at admin@lifemathmoney.com
Who Made This
This project was collaborated on by Harsh Strongman and Sergio.
Harsh Strongman is a Chartered Accountant and entrepreneur. He has a self-taught education in Computer Science. He is the owner of Life Math Money, the #1 self-improvement website for men. He can be found on Twitter, Instagram, and Telegram. Sign up for his free weekly newsletter here.
Sergio is an aerospace engineer by education, and has worked at Amazon (developing Alexa) as a software engineer. Currently, he works at eBay. He is also a Certified Professional Cloud Architect (Google Cloud), and is the owner of Your Coding Teacher, a website aimed at helping you supercharge your career. He can be found on Twitter, Instagram, and Telegram. His newsletter signup is available on the sidebar of his website.
Special thanks to Ash for being our alpha-test student and providing us with valuable feedback along the way.
Inspiration
The inspiration for this course comes from the Computer Science OSSU and Teach Yourself Computer Science.